They’re often cited as the ultimate security device, for those who really want to protect their connections. However a team of London and Italian based researchers have suggested that some of the top commercial VPNs are not quite as secure as they suggest. In fact in the study 14 of the top commercial VPN providers, all of them have displayed significant security problems
The study between the Sapienza University of Rome and Queen Mary University, London suggest that the promises of security are often not quite as valid as they suggest and user’s data is not adequately protected when using these particular VPN services.
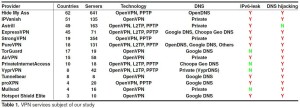
The study focussed on the known vulnerability of IPV6 traffic leakage, which was explained in the report – A Glance through the VPN Looking Glass. They checked these commercial providers to see if they suffered from the same vulnerability. The study focussed on the client software versions including all the biggest companies like HMA and IP Vanish.
Of course for many people, the VPN is not so much a security tool but a method for bypassing geo-blocks which restrict access based on their locations. In fact it’s arguably the most popular use of these tools, you can see the relative benefits of buying a US IP address through a USA proxy on this site – http://www.proxyusa.com/usvpn. It is fair to say that although security is a concern to many of these people, the ability to hide location from a web site is the primary goal.
The study was initially focussed on general exploration however it soon became apparent that there was a serious vulnerability to which all the major providers were subject to. The problem was IPV6 traffic leakage which allowed data from IPV6 traffic to be leaked through the native interface. The more extended attack based on two IPV6 DNS hijacking attacks which allowed an attacker to gain access to all of the users traffic.
One of the big problems was that all these services despite their ‘secure’ credentials relied on outdated technologies like PPTP and MS-CHAPV2 which both can be attacked using simple brute force methods. Although the vulnerabilities look like they’re only concerned with IPV6 the problem actually can expose all the users traffic and browsing history, even in the case of web sites which only accepted IPV4 traffic.
The report suggested some counter measures which included some simple changes based on modifying IPv6 routing tables to capture all the traffic and ensuring that the DNS services can only be accessed through the VPN tunnel and nowhere else.